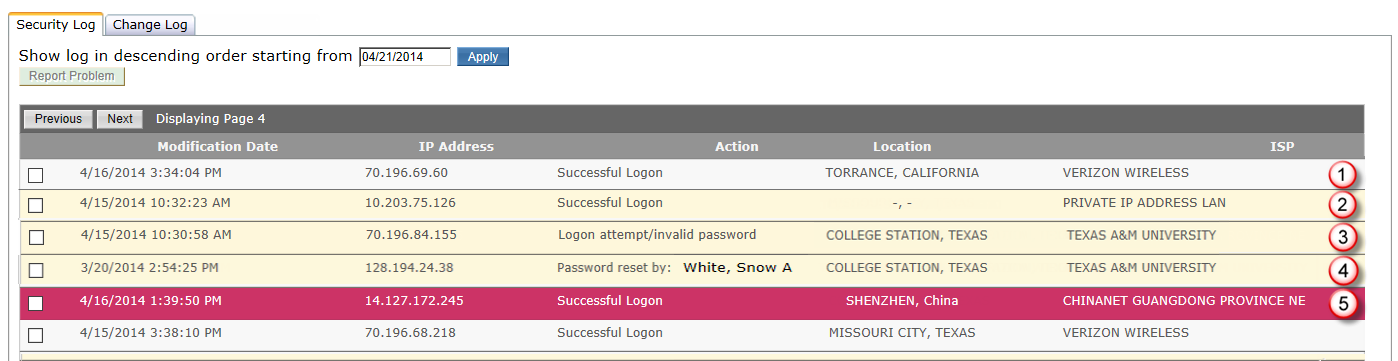
Not all highlighted actions need to be reported as a problem. In fact, most highlighted actions will be from actions initiated by an employee such as entering an invalid password or requesting a password reset.
However, these same actions could also be an attempted security breach if they were initiated by someone other than the employee. By color-coding these actions, an employee is warned about the activity so that they can determine if the activity is legitimate.
In addition to the color-coded warnings on the Security Log, the Home tab will display a message at the top of the page if a notable activity has occurred since the last logon. (To clear the message, the employee will need to click on the Log tab.)
Types of Warnings
A color-coded activity does not necessarily mean that something is wrong. It is meant to be a visual cue for an employee that there was an action on the Security Log that they may be interested in knowing about.
- White is the default color and is not a warning.
- Yellow represents a warning for an action that is worth noting.
- Red represents a severe warning that may require further action by the employee.
Below are examples of common actions that an employee may see on their log.
- This is a successful logon action and uses the default white color. It is not a warning.
- This is a successful logon action but it is colored yellow because the IP Address location could not be determined or the location is from outside of the United States. (See the note about IP Address locations below)
- This is an unsuccessful logon attempt and is colored yellow. This can happen when an employee enters their password incorrectly.
- This is a password reset and is colored yellow. A password reset can be initiated by an employee or by an administrator. The name of the person initiating the reset will be displayed.
- This is a red warning and occurs when an action occurs from an IP Address location in a country where known Phishing or hacking attempts have originated. However, the logon attempt could have been by an employee working or visiting one of those countries so further research may be needed.
– Note about IP Address locations – Because of the technologies used in determining geolocations of an IP Address, there are some inherent limitations when trying to accurately identify the exact location of an IP Address, such as
- SSO uses a database that is continually updated with information about IP Addresses and their ISPs. The location for an IP Address is only as accurate as the most recent update.
- IP Address locations from a cellular network may be misleading due to the way that internet traffic is routed between static and dynamic IP addresses.
- Some IP address ranges are designated as private. These are intended for use on an internal network within large organizations and aren’t meant to be accessed by the general public. For example, “TAMULINK”, the wireless network used by TAMU in the College Station area, uses a range of private IP addresses. Because these IP Addresses are “non-listed”, their locations cannot be determined.
- The name of the ISP and the time of the logon will usually be the most useful information in trying to determine if the logon attempt was made by an employee.
Each of the examples listed above could represent normal activity by an employee. The actions could also be from someone using the employee’s credentials to log into SSO. The purpose of color-coding the individual actions is to make an employee aware of these security related actions so that they can determine whether the action was one that they initiated.
Report a Questionable Activity
If it has been determined that an action on the Security Log is questionable and a cause for concern, it can be quickly reported to a security administrator by checking the box next to the action and then clicking the ‘Report Problem’ button. See the SSO FAQ, “How do I report a questionable logon activity?”